Data privacy engineering: built-in NOT bolted-on
Privya’s cloud-native approach enables Data Privacy by Design, so privacy and data protection is dealt with as part of the development life cycle, preventing future compliance violations.

The Privya Approach

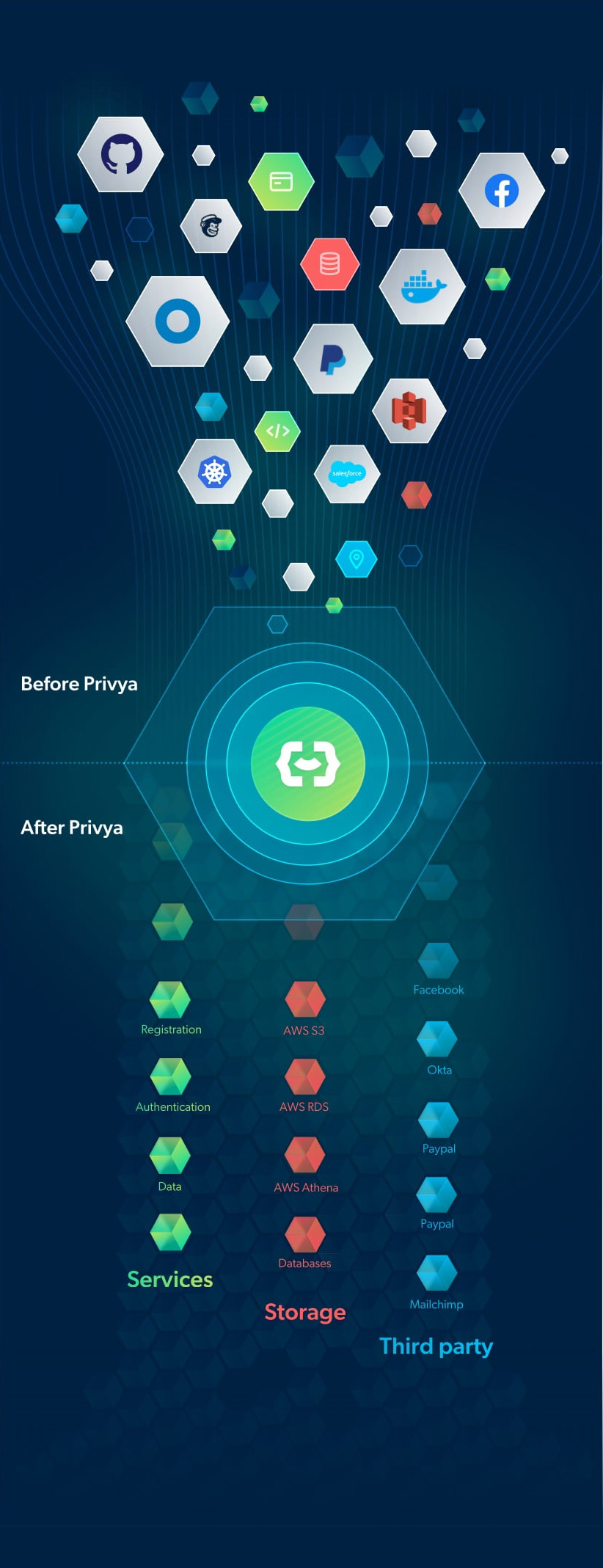
Automated data discovery & mapping
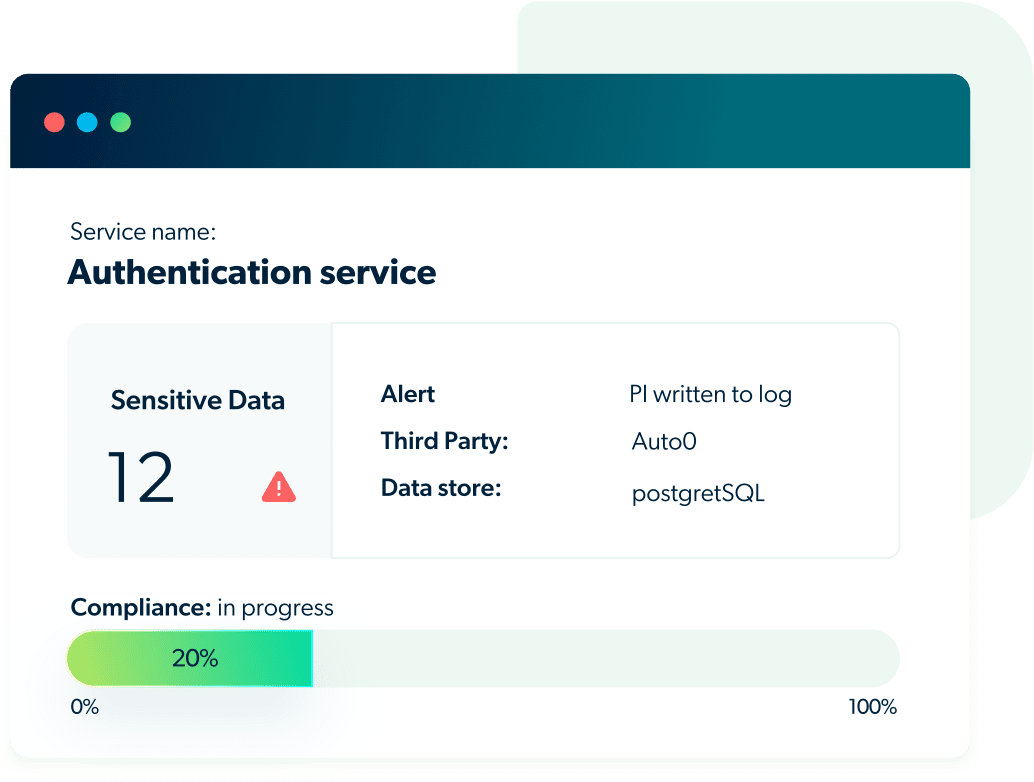
Identify data protection regulations automatically
Ensure Engineers, DPOs and GRCs speak the same language
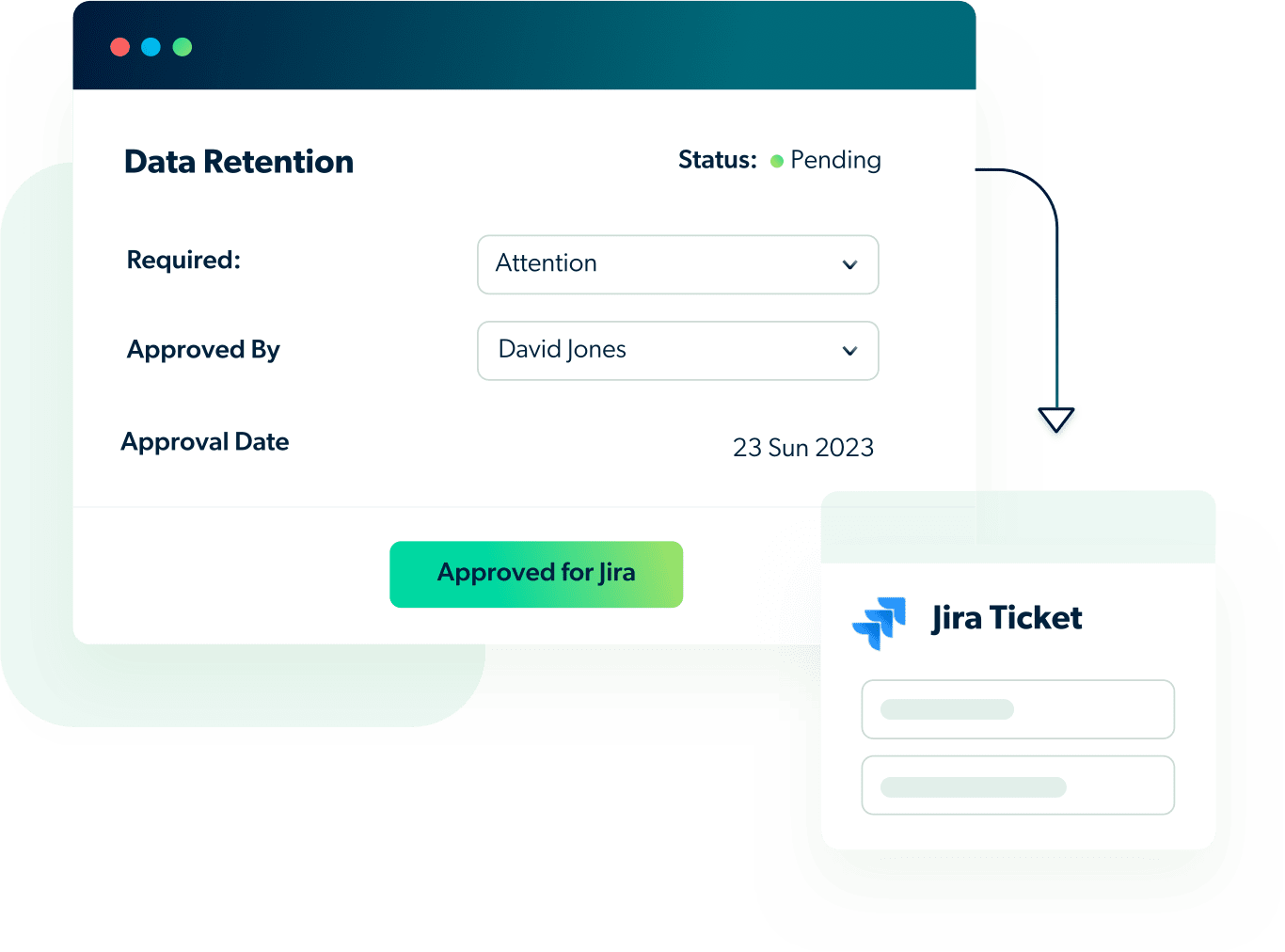
Simple, fast onboarding
Integrated into your CI/CD pipeline
Get an Analysis
Within 1 Hour
Privya FAQ
In short, Privya is a privacy management and privacy control, SaaS, AI-based solution. Privya bridges the gap between privacy professionals and engineers.
Privya is your centralized hub to manage and control your privacy program across your cloud native environments. Our cutting-edge privacy scanner abstracts the code and ties together all of your privacy management into a SaaS based management platform, by grouping together PI usage, data usage, storage and third party integrations from a privacy compliance perspective. By serving as an agentless privacy management solution that can be onboarded non-intrusively, we enable visibility, both into your legacy and new code at any stage of the software development lifecycle, and provide contextualized remediation plans.
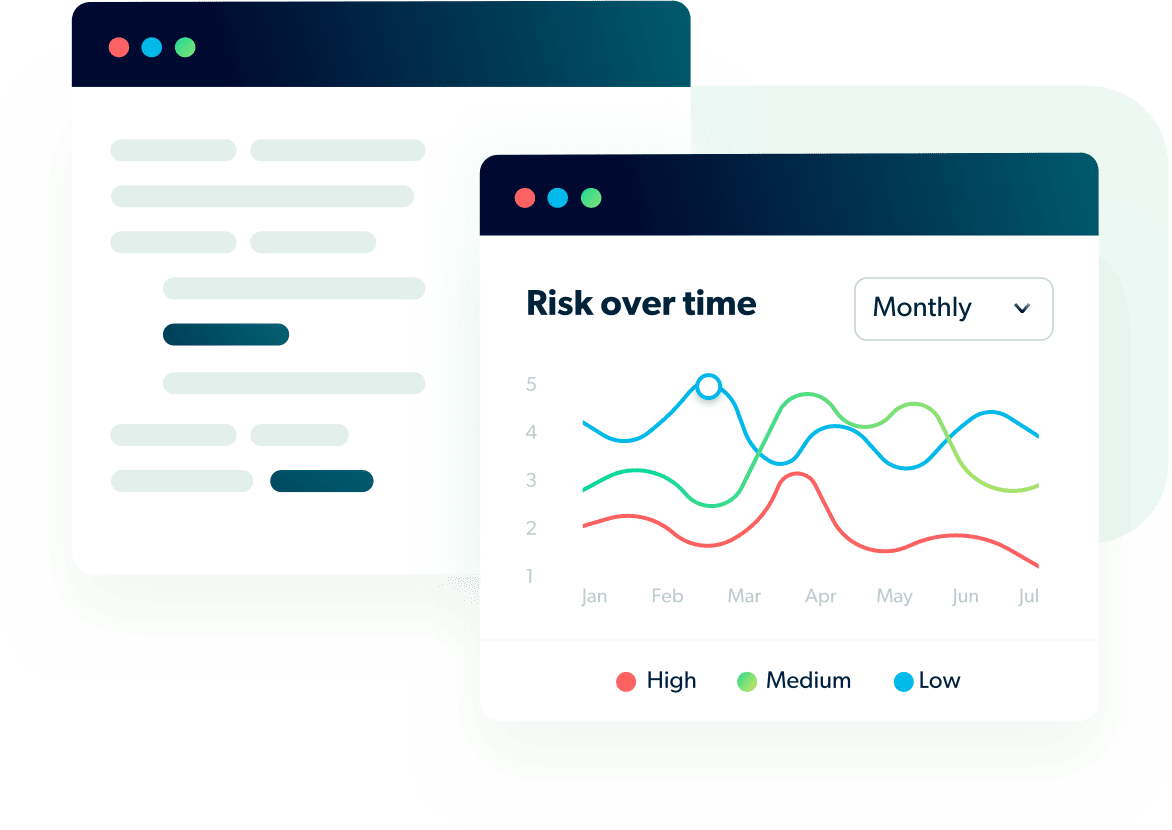
Measure the performance of your privacy program in one place with built in insights and guidance on data retention, data minimization, 3rd party, PI data sharing, lack of opt outs, usage of automatic profiling, enforcement and other privacy & data protection liabilities.
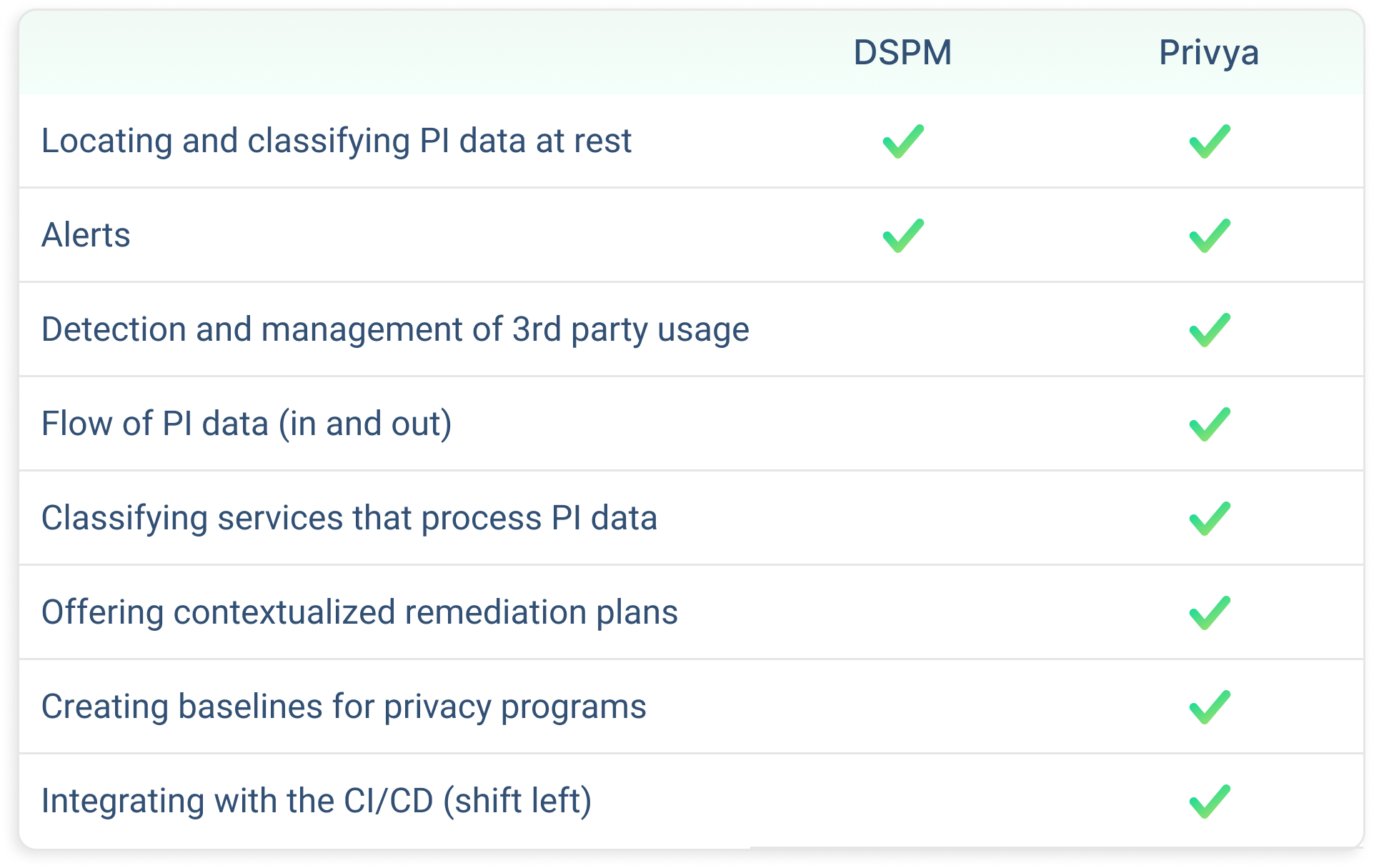
Data Security Posture Management (DSPM) tools are built to locate & classify PI data in storage of production environments in the cloud.
DSPM tools have been around for years, and while they are certainly excellent for generating visibility and detecting vulnerabilities of data assets in production environments, those same tools lose significance when managing privacy and data protection programs across all stages of the development life cycle.
The greatest weakness of DSPM tools is that they capture a very narrow and fragmented view of the data protection landscape, and lack capabilities to uncover data points that lead to deeper insights. For example, DSPM tools are unable to detect sharing of PI data with third parties, or provide a mapping of services, which are involved in the processing of personal data. Even when using DSPM tools, professionals are still left with tying together many different pieces of independent data and “connecting the dots”.
Privya determines data privacy and data protection risks by analyzing the data flow in your codebase, data sharing with third parties, storage usage and more. Also, Privya’s insights guide and advise businesses on how to best protect their data and mitigate risks. Privya applies its cutting-edge technology and best practices from a privacy engineering point of view, to prioritize issues that can lead to major breaches or violations.
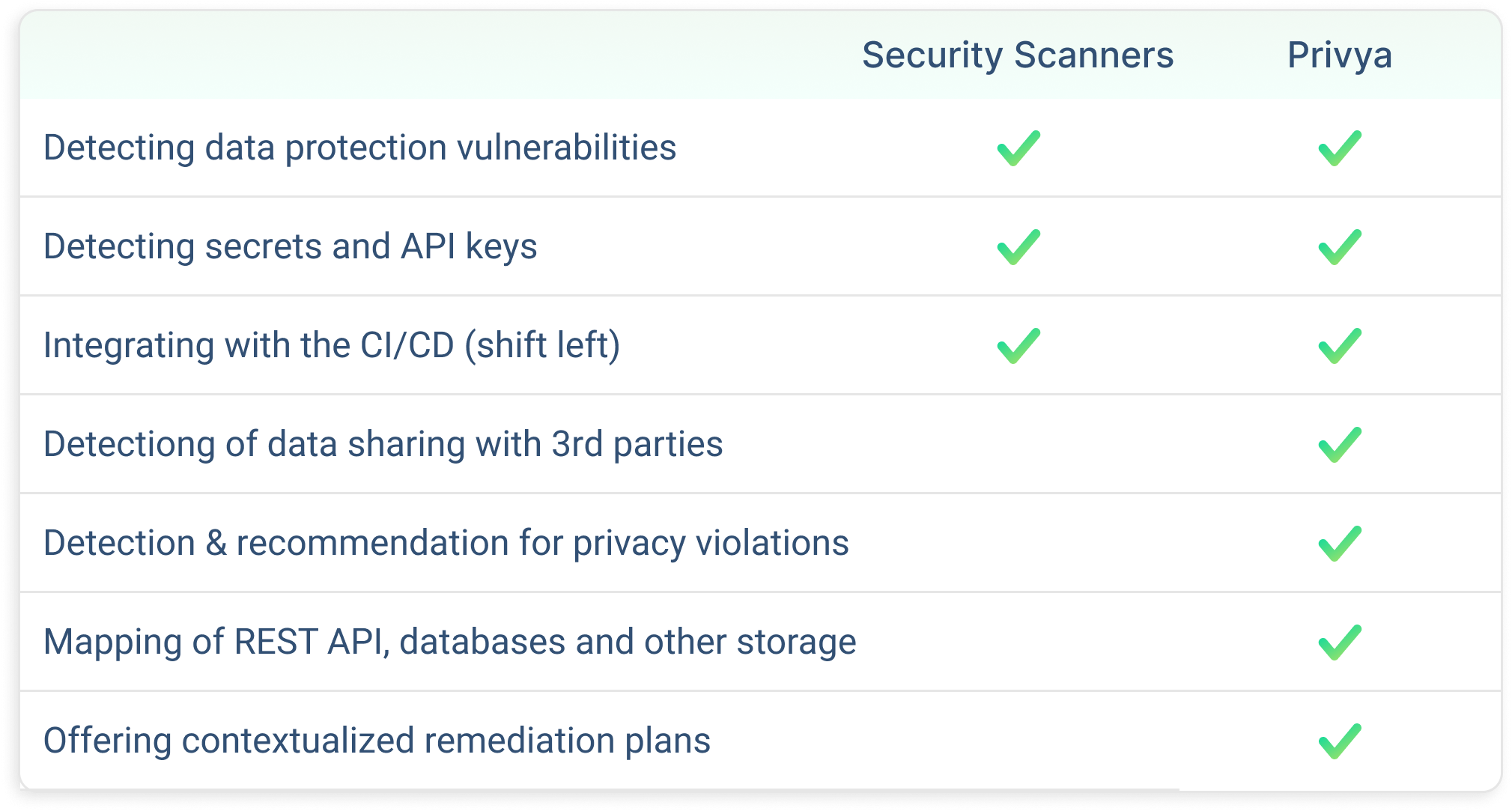
Privya’s privacy scanner is unlike traditional scanners and SAST tools, which are great for detecting security vulnerabilities, such as finding SQL injection possibilities or other trouble spots that malicious actors could exploit.
Privya’s privacy scanner, on the other hand, is purpose-built to deliver contextualized mitigation plans based on detection of privacy and compliance risks. Privya’s unique scanner abstracts your code, by grouping together PI usage, data usage, from a privacy compliance perspective.
Also, relying on traditional security and SAST tools to assist in your privacy efforts is like trying to fit a square peg into a round hole. While there is a little bit of overlap between privacy and security, security tools fail to take into account privacy violations and illegitimate processing of data.
The bottom line is that security vulnerabilities are not, and should not be treated the same as privacy risks. Privya helps privacy professionals to then ask bigger questions about your organization’s privacy management program.
Privacy practices are put in place to ensure the proper handling & managing of data without compromising a user’s identity. Regulations like the GDPR say personal data must be used in a way that is fair. This means you must not process the data in a way that is unduly detrimental, unexpected or misleading to the individuals concerned. For example, let’s examine the opt-out of data sharing. After a user opts out of a service, organizations are required to delete personal data, which may become more complex, especially considering legacy code, as well as third party apps or data brokers.
Skipping even the smallest of steps in protecting their customer data may lead to huge losses and irreparable damages. Practical data privacy policies and concerns cater to:
- Data collection and storage
- Data sharing with third parties
- Data retention
- Opt-out
- Automatic profiling on personal data
- Complying with regulations such GDPR, CCPA, NIST, HIPAA
Security, on the other hand, is about finding a weakness, vulnerability, or error found within a system that can be leveraged by a threat agent in order to compromise a secure network. This is not the same as privacy.
