



Unveiling the Power of AI
Security Intelligence for the Modern Enterprise
At Next.sec(AI), we've pioneered a groundbreaking approach to AI security that fundamentally transforms how organizations protect their AI systems. Our innovative technology delivers comprehensive security coverage across the entire AI lifecycle - from development environments to production deployments - without requiring runtime agents or impacting system performance. By analyzing code, models, and infrastructure before deployment, we help organizations build secure AI with confidence.
Our Technology at a Glance

AI/ML Supply Chain Analysis
We leverage advanced static analysis techniques to decompose your entire AI ecosystem into its fundamental components, enabling us to map dependencies, track data flows, and identify security risks before they reach production. Our system analyzes everything from Jupyter notebooks to production models, providing unprecedented visibility into your AI/ML supply chain.

Model Security Validation
Our proprietary algorithms perform deep inspection of AI/ML models and their training pipelines, detecting malicious models, and usage of sensitive data. This allows us to detect vulnerabilities like model poisoning, data leakage, and tampering attempts before they can impact production systems.

Graph Intelligence Technology
Through sophisticated graph analysis techniques, we construct a comprehensive representation of your data pipeline infrastructure that reveals hidden relationships, violations in the usage of PII data, and potential attack paths. This graph-based approach enables us to identify complex security risks that traditional tools miss by understanding the interconnections between models, data, and infrastructure.

AI-Powered Security Posture Analysis
Combining statistical analysis, machine learning, and expert security rules, our platform automatically discovers security issues across your AI development lifecycle. This includes scanning for exposed secrets, vulnerable dependencies, and compliance violations while providing actionable remediation guidance.

ML Framework Recognition
Our extensive knowledge base understands security patterns across internal and external AI/ML frameworks and services, allowing us to detect framework-specific vulnerabilities and misconfigurations. We continuously update our security AI/ML database to stay ahead of emerging threats in the AI ecosystem.
The Visionary Behind the Innovation:
Dr. Uzy Hadad
Dr. Uzy Hadad is the co-founder and CTO of Next.sec(AI). Inspired by the recent improvement in large language models (LLMs) and the ability to consider code as a natural language (like in AI code generators such as Co-Pilot), Dr. Uzy has devoted his research to the study of graph theory and its practical applications in computer science. With over a decade of experience in data engineering, data science, and global technology transformation, Dr. Uzy's work has revolutionized how we understand and visualize complex data relationships.
His academic background includes a PhD in Mathematics and Computer Science from The Hebrew University of Jerusalem and post-doctoral studies in Mathematics and Computer Science at the Weizmann Institute of Science, one of the highest-ranked institutions globally. Dr. Uzy's pioneering work in applying graph theory and machine learning to static code analysis has laid the foundation for Next.sec(AI)'s unique approach to data lineage. His algorithms have redefined what's possible in terms of understanding data flows without runtime execution, bridging the gap between engineering, privacy, compliance, and data protection teams.



– Dr. Uzy Hadad
In-Depth Technology Breakdown
Development Security
Key Features:
- Advanced static analysis technology that decomposes Jupyter notebooks and AI code into abstract syntax trees, enabling precise detection of security issues like exposed secrets, vulnerable dependencies, and potentially malicious code patterns that could compromise model integrity
- Comprehensive scanning of ML development environments that automatically identifies and tracks all AI assets, including models, training data, and third-party components to eliminate shadow AI and ensure complete visibility
- Sophisticated dependency analysis system that maps the entire AI supply chain to detect vulnerable or malicious packages before they can impact production systems or compromise model security
- Automated security validation of model serialization and storage mechanisms that prevents common attack vectors like pickle exploits while ensuring secure model persistence and loading
- Continuous monitoring of development artifacts that detects security drift and ensures ongoing compliance with security policies and regulatory requirements throughout the AI development lifecycle
Technical Deep Dive:
- Integrated development environment scanning that provides security coverage across Jupyter, VSCode, PyCharm, and other popular AI development tools
- Framework-specific security rules that understand security patterns in PyTorch, TensorFlow, scikit-learn, and other major ML frameworks
- Platform security analysis that validates configurations across AWS SageMaker, Azure ML, Google Vertex AI, and other MLOps platforms
- Data pipeline security coverage that ensures sensitive data is protected across Spark, Airflow, dbt and other data processing tools
- Model registry scanning that validates security controls in MLflow, Weights & Biases, and other model management systems

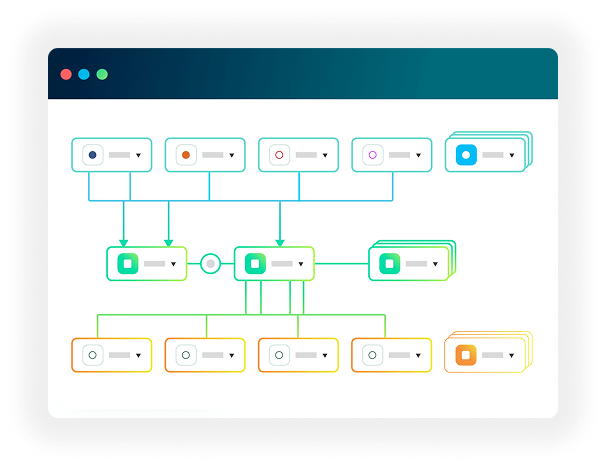

Model & Data Security
Key Features:
- Advanced model validation system that performs comprehensive security analysis of model architectures, weights, and parameters to detect signs of tampering, backdoors, and malicious modifications during training or deployment phases
- Sophisticated training data security analysis that examines data pipelines for potential leakage of sensitive information, validates privacy controls and ensures compliance with data protection regulations across the entire model lifecycle
- Multi-layered defense system against model inversion attacks that combines access controls, differential privacy techniques, and continuous monitoring to prevent unauthorized extraction of training data from model outputs
- Proactive identification of membership inference vulnerabilities through automated testing that simulates potential attacks and validates privacy-preserving mechanisms before models reach production
- Comprehensive transfer learning security framework that monitors fine-tuning processes, validates base models, and detects potentially malicious knowledge transfer between models
Technical Deep Dive:
- Multi-stage defense system against input manipulation and data poisoning that validates training data integrity, monitors data pipelines, and detects anomalous patterns in model behavior
- Advanced model protection mechanisms that prevent unauthorized access, monitor usage patterns, and detect attempts to extract model architecture or parameters
- Runtime integrity validation system that ensures model outputs haven’t been tampered with and maintains end-to-end security of inference pipelines
- Continuous supply chain monitoring that detects compromised components, validates package integrity, and prevents introduction of malicious dependencies


Supply Chain Intelligence
Key Features:
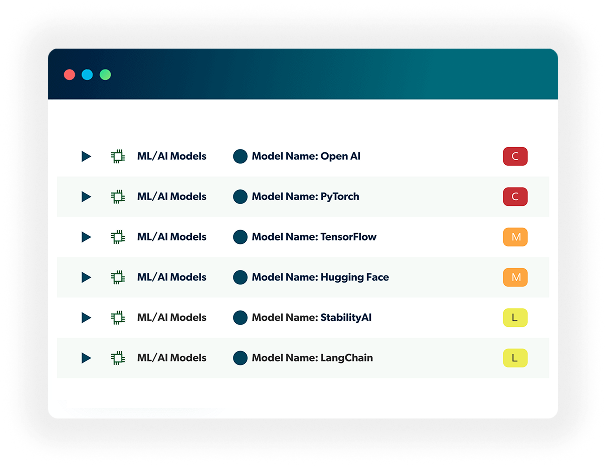
- Automated AI Bill of Materials (BOM) generation that provides complete visibility into all AI components, including models, training data, libraries, and runtime dependencies across your entire AI infrastructure
- Sophisticated third-party AI detection system that identifies embedded AI capabilities within commercial software, cloud services, and open-source components to maintain comprehensive security coverage
- Advanced vulnerability scanning technology that continuously monitors dependencies for known issues, zero-day threats, and potential security risks specific to AI/ML components
- Comprehensive license compliance monitoring that tracks open-source usage, validates licensing requirements, and ensures regulatory compliance across your AI supply chain
- Dynamic attack surface mapping that visualizes potential entry points, identifies critical vulnerabilities, and prioritizes security risks based on potential business impact

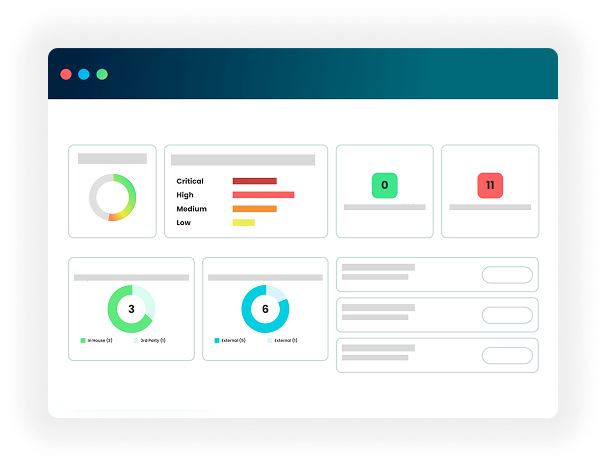
Compliance & Governance
Key Features:
- Automated compliance framework that maps security controls to requirements from EU AI Act, NIST AI RMF, and other relevant regulations
- Sophisticated evidence collection system that automatically gathers and organizes documentation needed for security audits and compliance reviews
- Advanced risk assessment engine that evaluates AI systems against regulatory requirements and generates detailed reports for stakeholders
- Real-time compliance monitoring that tracks adherence to regulatory requirements and alerts on potential violations
- A comprehensive governance framework that enables organizations to define, implement, and enforce AI security policies



Audit Capabilities
Privya offers comprehensive audit features to ensure accountability and transparency:
Tamper-Proof Audit Trail
- An immutable record of all user actions on the Privya platform
- Captures every interaction, modification, and access attempt
- Ensures complete visibility for compliance and security purposes
Granular Access Controls
- Enforces least privilege principle
- Supports separation of duties
- Customizable user roles and permissions
Historical Audit Retention
- Maintains comprehensive historical metadata for audit purposes
- Enables trend analysis and long-term compliance tracking
Regulations Supported
Next.sec(AI) offers robust support for a wide range of global privacy compliance standards, including:

GDPR
General Data Protection Regulation

CPRA/CCPA
California Privacy Rights Act/California Consumer Privacy Act

HIPAA
Health Insurance Portability and Accountability Act

GLBA
Gramm-Leach-Bliley Act

PCI DSS
Payment Card Industry Data Security Standard

OCPA
Ohio Consumer Privacy Act

ICDPA
Indiana Consumer Data Protection Act

VCDPA
Virginia Consumer Data Protection Act

MHMDA
Mental Health Modernization and Data Accountability Act

DTDPA
District of Columbia Personal Data Protection Act

CPA
Colorado Privacy Act

EU AI Act
EU Artificial Intelligence Act

NIST RMF
National Institute of Standards and Technology Risk Management Framework
Integration & Deployment

Enterprise Integration
- Seamless integration framework that connects with existing security tools including SIEM platforms, SOAR systems, and security analytics solutions
- An advanced identity management system that works with enterprise IAM providers to ensure consistent access control and authentication
- Sophisticated ticketing integration that streamlines security workflows and accelerates incident response through automated ticket creation and routing
- Comprehensive cloud platform support that enables security monitoring across AWS, Azure, Google Cloud and other major providers
- Developer-friendly integration options including APIs, webhooks, and custom connectors for various development tools and platforms
Compliance and Security Features
Next.sec(AI) implements robust security measures to protect sensitive data and ensure platform integrity

SOC 2 Type II Attestation
- Demonstrates adherence to strict information security policies and procedures
- Ensures the highest levels of security, confidentiality, and integrity

Advanced Authentication
- Single Sign-On (SSO) support
- Identity federation capabilities
- Multi-factor authentication options

Data Protection
- Advanced encryption for data at rest and in transit
- Secure, geographically distributed data centers for SaaS offering

Network Security
- Sophisticated network segmentation
- Intrusion detection and prevention systems
- Regular security audits and penetration testing

Secure Development Practices
- Follows secure software development lifecycle (SDLC) principles
- Regular code reviews and security testing
Conclusion
Privya’s cutting-edge technology offers a comprehensive solution for data privacy, compliance, and governance. By leveraging advanced AI and machine learning, we provide unparalleled insights into your data ecosystem, ensuring compliance, reducing risk, and enabling confident innovation in today’s complex data landscape.
