Secure AI Systems from Source to Production
Next.sec(AI) AI-SPM and Supply Chain Security Platform Identifies Hidden Attack Vectors that Others Don’t from Source Code to Models, Policies, and Third-party AI Dependencies
Our revolutionary approach transforms how organizations secure their AI systems. While others monitor AI in runtime, we analyze your complete ML/AI supply chain—including models, notebooks, third-party libraries, and development artifacts—to identify security risks and compliance issues during development. No performance overhead, and no operational complexity.
Discover Next.sec(AI) for:

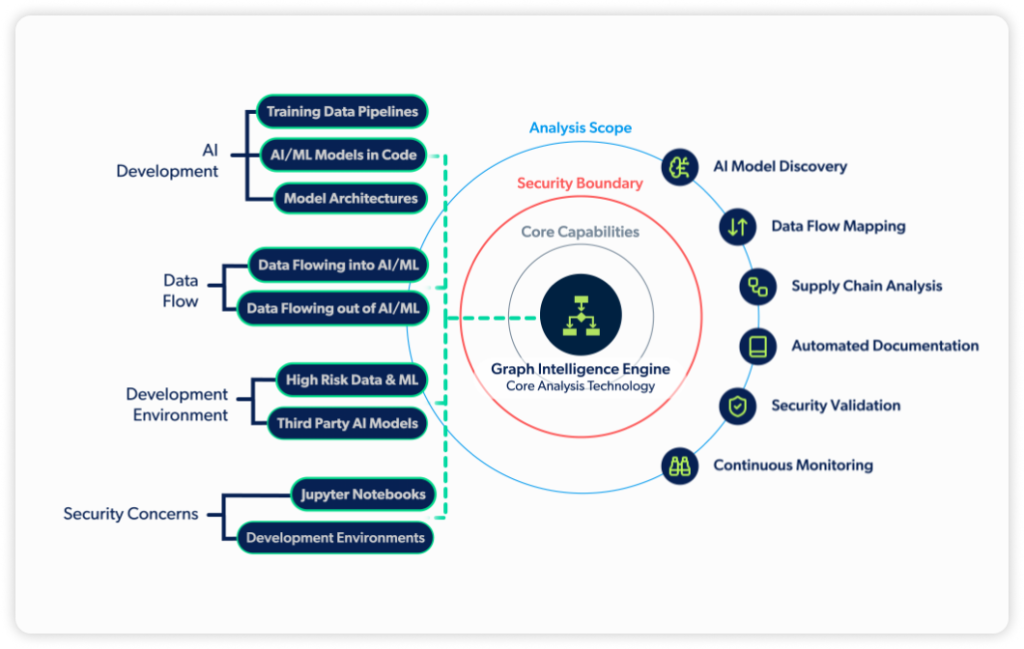
Our Unique Edge: AI-Powered Code Analysis
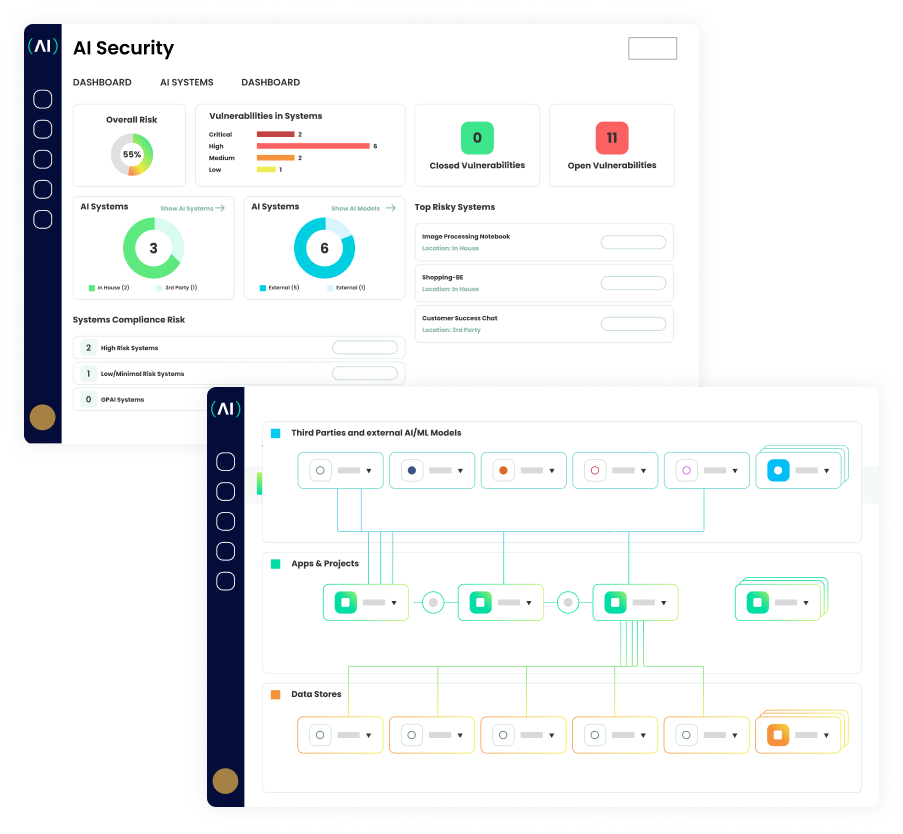
Next.sec(AI) AI ecosystem supply chain analysis delivers what runtime monitoring can't:
Secure AI/ML Solutions: Protect your entire AI ecosystem including models, training data, and third-party AI components from security threats
Proactive Risk Detection: Identify security vulnerabilities and PIIs across your AI supply chain before deployment through code analysis rather than reactive runtime monitoring
Complete Visibility: Map your entire AI supply chain including data flows, sensitive information, dependencies, and third-party components
Zero Runtime Overhead: Eliminate performance impact and operational complexity of runtime monitoring tools
Comprehensive Coverage: Analyze everything from Jupyter Notebooks to production code to identify hidden risks
Trusted by Industry Leaders
Next.sec(AI) detection of secrets, PII, and mapping helps us keep data secure. It saves time and resources, but most importantly –
we know our students’ privacy is protected.”

Michael Manrod
Chief Information
Security Officer
Implementing Next.sec(AI) was a game-changer for data privacy compliance. We didn’t have to spend hours going through code, and my engineers can focus on their core tasks instead of manual compliance checks.”

Etzik Bega
Chief Security and
Chief Privacy Officer,
BlackSwan

Empower Your Team Across Key Use Cases

Security Teams
- Eliminate blind spots in your AI security posture
- Track and secure your entire AI supply chain
- Prevent rather than detect security incidents

AI Development Teams
- Ship secure AI applications with confidence
- Identify vulnerable dependencies before integration
- Validate security requirements during development, not after

Compliance Teams
- Streamline EU AI Act and NIST AI RMF compliance
- Maintain continuous regulatory readiness
- Automate compliance evidence collection
Features That Drive Compliance

Intelligent AI Security Scanning
Generate comprehensive AI Bill of Materials (BOM); Automatically detect malicious models, vulnerabilities, exposed secrets, and compliance issues in AI code and notebooks.

Supply Chain Intelligence
Map every component in your AI systems and track security posture across your entire AI supply chain.
Continuous Security Validation
Validate security controls and compliance requirements with every code change.

Risk-Based Insights
Prioritize security issues based on actual risk to your AI systems and business.

Developer-First Integration
Seamlessly integrate with existing development tools and workflows including Colab, Jupyter, GitHub, GitLab, and major CI/CD platforms.
Discover the Next.sec(AI) advantage
As AI becomes critical to business success, securing it becomes critical to business survival. Next.sec(AI) transforms how organizations secure their AI systems by catching risks at the source - in code. Whether you're developing new AI applications or securing existing ones, we help you ship secure AI with confidence.
Start securing your AI systems today with zero impact on performance or productivity.
